Porting Doom to a payment terminal

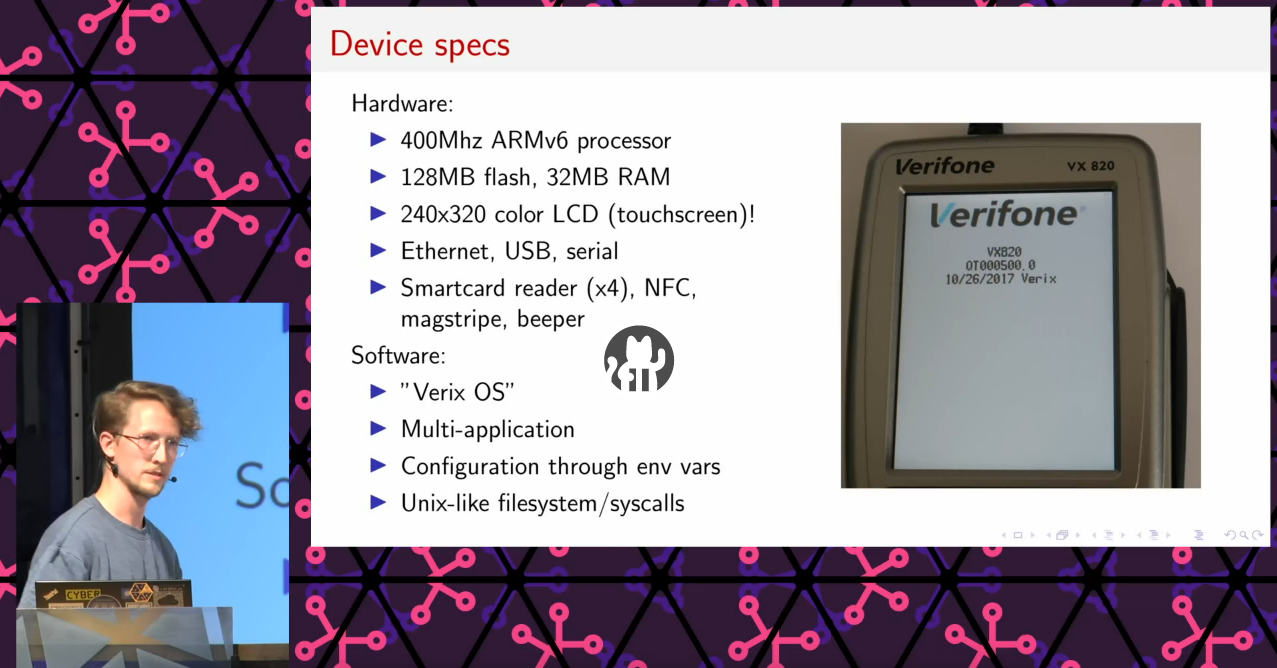
For the past half a year or so I have been playing around with a specific type of payment terminal, the VX820 from Verifone.
I randomly bought a couple of second-hand devices, and found out that they are wonderful pieces of hardware with lots of potential for alternative uses. I figured that a fun goal for myself would be to port Doom to it, which would nicely showcase the device’s unexpected computational power.

This is not even my complete collection...
About half a year later, I have a ton of notes, hacky scripts, patched binaries, and a working version of Doom. To achieve this, I made use of a previously discovered and mitigated bootloader vulnerability (credits and link below), which was apparently not patched on my devices. The full background story, including some high-level details of the exploit approach were described in my talk at May Contain Hackers (MCH2022) (video, slides).
Talk on Verifone POS hacking at May Contain Hackers (MCH2022).
On openness
I have decided not to publicize all the {code,binaries,scripts,notes} from my research, considering bad actors could easily use this approach to flash and sign spoofed payment applications on devices that are in active use.
This decision was strenghtened by the fact that 80% of the devices I bought second hand had unpatched (out-of-date) bootloaders, even though almost all of them appeared to have been used very recently. And this was only in the Netherlands.
Nevertheless, if you are interested and have access to a vulnerable device, you should be able to reproduce the attack from my description, and from the earlier research.
Links
- https://github.com/ThomasRinsma/pyxdl
- An open implementation of Verifone’s XDL download protocol. This can be used both in the system menu and in the bootloader.
- POSWorld: Vulnerabilities within Ingenico Telium 2 and Verifone VX and MX series Point of Sales terminals
- Previous research from the Payment Village. These guys found the bootloader vulnerability and described the application authentication system. Both of which are used in my exploit.
- https://github.com/ozkl/doomgeneric
- An easily-portable version of Doom which I based my port on.
Videos
Game of Life and Doom running on the VX820:
Photos
For those interested in what’s inside. Click on a thumbnail to view the full-resolution photo.
❦